
Yakub Usmonovich Usmonov
All sciences. №7, 2022. International Scientific Journal
Used literature
1. Mendelson E. “Introduction to mathematical logic”. – M. Nauka, 1971.
2. Edelman S. L. Mathematical logic. – M.: Higher School, 1975. – 176 p.
3. Igoshin V. I. Taskbook-practical course in mathematical logic. – M.: Enlightenment, 1986. – 158 p.
4. Gindikin S. G. Algebra of logic in problems. – M.: Nauka, 1972. – 288 p
.5. Barabanov O. O. Implication / Proceedings of the XI International Kolmogorov readings: collection of articles. – Yaroslavl: YAGPU Publishing House, 2013. pp.49—53.
INFORMATION TECHNOLOGY
A WAY TO PROTECT INFORMATION FROM UNAUTHORIZED ACCESS TO THE VOLS
UDC 004.056
Kuldashov Obozjon Khakimovich
Doctor of Technical Sciences, Professor of the Scientific Research Institute “Physics of Semiconductors and Microelectronics” at the National University of Uzbekistan
Komilov Abdullazhon Odiljon ugli
Assistant of the Fergana branch of the Tashkent University of Information Technologies named after Muhammad al-Khorezmi
Ferghana branch of Tashkent University of Information Technologies named after Muhammad al-Khorezmi
Annotation. The article proposes a method for protecting an information signal from unauthorized access in a fiber-optic communication line, provides a block diagram and the principle of operation of the device.
Keywords: fiber-optic line, communication, information signal, protection method, device, block diagram.
Аннотация. В статье предложен способ защиты информационного сигнала от несанкционированного доступа в волоконно-оптической линии связи, приведена блок схема и принцип работы устройства.
Ключевые слова: волоконно-оптическая линия, связь, информационный сигнал, способ защиты, устройство, блок схема.
In recent years, one of the most promising and developing areas of building a communication network in the world is the VOLS.
The priority direction of the development of the transport network of Uzbekistan is the transfer of the network to the widespread use of fiber optic networks with digital transmission systems.
This made it possible to organize reliable high-quality communication not only between the “telephone continents”, but also communication on the National Telecommunications Network of Uzbekistan. The realization of this task has become possible since 1997 after the completion of the construction and commissioning of the national segment of TAE – a large-scale international project “Trans-Asian-European VOLS”.
In 2011, the task was to ensure the development and modernization of the telecommunications network based on the introduction of modern broadband and optical technologies, the introduction of over 950 kilometers of fiber optic lines, the expansion of the data transmission transport network to regional centers.
Throughout the country, at the level of district centers, obsolete analog telephone exchanges have been replaced with modern digital ones. High-speed digital channels have been created on the basis of the VOLS, work is underway to expand the network and improve its reliability. The created infrastructure serves as the basis for the rapid development of wireless technologies, in particular, mobile communications. As a result, the level of coverage by the digital telecommunications network of regions, district centers and cities of the Republic amounted to 100 percent, the level of coverage by the telecommunications network of rural settlements – 95.7 percent.
In 1999—2000, at the expense of the funds of the Cooperation Fund for Economic Development of the Republic of Korea (EDCF), technical re-equipment and development of the telecommunications network in the Andijan and Ferghana regions were carried out, a 354 km long fiber-optic line was built, switching equipment with a capacity of 46 thousand numbers was installed.
The widespread use of fiber-optic telecommunication systems in communication networks is due to a number of their advantages in comparison with electrically cable communication systems.
Based on this, the following main advantages of a fiber-optic line can be distinguished in comparison with electric cable communication systems:
– huge bandwidth with transmission speeds of up to 40 Gbit/s, operating today, and over 100 Gbit/s, expected in the near future. The factors limiting the growth of transmission rates are currently the inertial properties of receivers and radiation sources. However, the use of the spectral compaction method (WDM, wave division multiplexing) increases the total transmission rate over a single fiber to several Departures/s;
– fiber optic cables are completely unaffected by electromagnetic interference, lightning and high voltage surges. They do not create any electromagnetic or radio frequency interference;
– ensuring complete galvanic isolation between the receiver and the information transmitter, as well as the absence of a short circuit in the transmission line;
– the distance of information transmission for low-cost fiber-optic cables between repeaters is up to 5 km. For high-quality commercial systems, the distance between repeaters is up to 300 km. Distances close to 1000 km have been achieved under laboratory conditions;
– the size and weight of fiber optic cables compared to all other data cables are very small in diameter and extremely light. A four-core fiber optic cable weighs approximately 240 kg/km, and a 36-core fiber optic cable weighs only 3 kg more.
From the above it follows that the VOLS meet all the requirements of modern telecommunication communication systems. In this regard, many experts in telecommunications technologies argue that the VOLS will become the main means of transmitting information in the future. However, with the growth of the use of fiber-optic information transmission lines in telecommunication systems and their development, technical information intelligence systems are also developing, with the help of which information is secretly taken from the VOLS.
All over the world, great attention is paid to ensuring information security – the state of security of the information environment of society, ensuring its formation, use and development in the interests of citizens, organizations, and the state.
Therefore, the development of effective methods and technical means for the protection of information in the VOLS is one of the urgent tasks.
Structural, mechanical and electrical technical means are usually used to protect information in the VOLS. Some of the types of protective equipment of this group are built in such a way as to complicate the mechanical cutting of the cable and prevent access to the S [1]. Similar means of protection are widely used in traditional wired networks of special communication. Also promising is the use of a pair of longitudinal power elements of the OK, which are two steel wires arranged symmetrically in a polyethylene shell, and used for remote power supply and monitoring of sensors installed in the couplings, and monitoring of ND. It is also advisable to use a kit to protect the welding site, which fills the welding site with an opaque solidifying gel. One of the proposed methods of protection is the use of multilayer optical fiber with a special structure of reflective and protective shells [2]. The construction of such a fiber is a multilayer structure with a single-mode core. The selected ratio of the refractive coefficients of the layers makes it possible to transmit a multimode control noise optical signal along the annular guide layer. There is no connection between the control and information optical signals in the normal state. Ring protection also makes it possible to reduce the level of radiation of an information optical signal through the side surface of the S (by means of leakage modes arising at the bends of the fiber of various sections of the communication line). Attempts to penetrate to the core are detected by changing the level of the control (noise) signal or by mixing it with the information signal. The location of the ND is determined with high accuracy using a reflectometer.
Many works are devoted to methods and means of information protection in the VOLS, including in [3] to protect information, the magnitude of the inhomogeneity of electromagnetic radiation propagation through a cable in the radio frequency range is controlled, which is introduced into a waveguide channel with a constant length of wave resistance, made in the form of an electrically conductive shell covering at least one electronic conductor, located along the fibers, and the presence of unauthorized access to the information transmitted through the fibers is judged by the change in the magnitude of the inhomogeneity of the propagation of electromagnetic radiation in the radio frequency range. The protection system contains a combined cable and a lock for changing the parameters of the propagation of electromagnetic radiation of the radio frequency range connected to an electronic conductor.
A method of protecting information from unauthorized access in fiber-optic communication lines is proposed and can be used in fiber-optic systems for transmitting confidential information.
Figure 1 shows a block diagram of a device implementing the proposed method of protecting an information signal from unauthorized access in a fiber-optic communication line. A device implementing the proposed method of protecting an information signal from unauthorized access in a fiber-optic communication line contains: on the transmitting side 1, an information signal generator 2, a mixer 3, a source 4 of transmitted optical radiation, a noise signal photodetector 5, a directional coupler 6 with inputs 6—2 and output 6—1, a fiber-optic communication line 7, on the receiving 8 side there is a directional 9 coupler with inputs 9—1 and output 9—2, a total signal photodetector 10, a mixer 11, delay lines 12, an inverse noise signal shaper 13, source 14 of noise optical radiation and generator 15 of noise signal.
When implementing the proposed method of protecting the information signal from unauthorized access in the fiber-optic communication line, the following operations are performed:
– on the receiving side 8 of the fiber-optic communication line 7:
1) generate a noise signal using the generator 15,
2) an inverse noise signal is generated using the inverter 13,
3) using the delay line 12, delays of the inverse noise signal are produced for a time,
4) modulate the transmitted optical noise radiation in the optical radiation source 14 with a noise signal,
5) the transmitted noise optical radiation is introduced through the input 9—1 of the directional coupler 9, into the fiber-optic communication line 7,
– on the transmitting side 1 of the fiber-optic communication line 7:
1) form the transmitted information signal using the shaper 2,
2) output through the output 6—1 of the directional coupler 6, from the fiber-optic communication line
7 of the received optical noise radiation,
3) a noise signal is generated from the received optical noise radiation using a photodetector 5,
4) form a total signal by mixing an information and noise signal using a mixer 3,
5) modulate the transmitted optical radiation in the source 4 of the transmitted optical radiation with a total signal,
6) the transmitted optical radiation is introduced through the input 6—2 of the directional coupler 6, into the fiber-optic communication line 7,
– on the receiving side 8 of the fiber-optic communication line 7:
1) the received optical radiation is output through the output 9—2 of the directional coupler 9 from the fiber-optic communication line 7,
2) a total signal is generated from the received optical radiation using a photodetector 10,
3) mixer 11 by shifting the delayed inverse noise signal to the total signal, an information signal is isolated
When using the proposed method of protecting an information signal from unauthorized access in a fiber-optic communication line, in which a noise signal is generated on the receiving side before the total signal is formed, which is transmitted to the transmitting side of the fiber-optic communication line for mixing to the information signal.
On the receiving side, in the process of shifting to the total signal, the delayed inverse noise signal occurs with a complete phase coincidence of the noise and its inverse signal. As a result, the noise signal is fully compensated, the information signal is allocated and the information in the fiber-optic communication line is protected from unauthorized access.
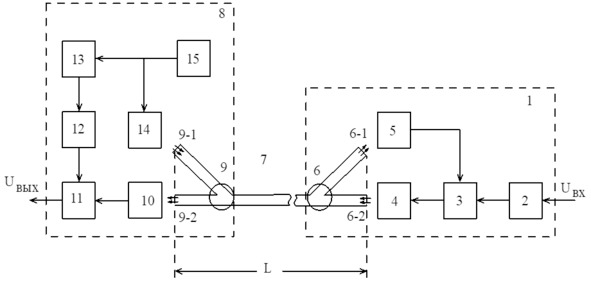
Fig. 1. Block diagram of the device
A method of protecting an information signal from unauthorized access in a fiber-optic communication line, consisting in the fact that an information signal is formed on the transmitting side of a fiber-optic communication line, a total signal is formed by mixing a noise and information signal, formed by modulating the total signal of the optical radiation to be transmitted and introduced into a fiber-optic communication line, and on the receiving side of the fiber-optic communication line, the received optical radiation is output from it, from the received optical radiation, a total signal is formed from which an information signal is isolated, characterized in that before the formation of the total signal, an initial and inverse noise signal is formed on the receiving side, modulated with the initial noise signal of optical radiation and injected into the fiber-optic communication line, and the received optical radiation is output from it on the transmitting side of the fiber-optic communication line, a noise signal is formed from the received optical radiation, which is subject to the displacement of the information signal, and the allocation of the information signal on the receiving side is made by mixing the delayed inverse noise signal to the total signal, and the delay time of the inverse noise signal is determined by the expression, where: L is the length of the optical fiber; v is the speed of optical radiation in the optical fiber.
Literature
1. Korolkov, I. A. Kraschenko, V. G. Matyukhin, S. G. Sinev. Problems of protecting information transmitted over fiber-optic communication lines from unauthorized access/ Information Society, 1997, issue 1, pp. 74—77
2. A. V. Boos, O. N. Shukhardin. Analysis of the problems of ensuring the security of information transmitted via optical communication channels and ways to solve them.//Informational counteraction to the threats of terrorism: scientific and practical. Journal. /FSUE STC, Moscow. 2005, No. 5. p. 172180.
3. K.E.Rumyantsev, I.E. Khayrov. Protection of information transmitted via LED communication lines..//Information counteraction to terrorism threats: scientific and practical. Journal. /FSUE STC, Moscow. 2004, No. 2. pp. 27 – 32.
COMPUTER MODEL OF MICRO-HYDROELECTRIC POWER STATION USING THE POTENTIAL ENERGY OF GEOTHERMAL WATERS
UDC 004.94
Kuldashov Obbozjon Xokimovich
Doctor of Technical Sciences, Professor of the Scientific Research Institute “Physics of Semiconductors and Microelectronics” at the National University of Uzbekistan
Dadazhonov Tulanboy
Senior Lecturer of the Department of Electronics and Instrumentation of the Fergana Polytechnic Institute
Fergana Polytechnic Institute
Annotation. A model of joint operation of a micro – hydroelectric power plant and a geothermal water facility has been developed, taking into account their main technical and technological characteristics in a wide range of operating conditions, including rotor rotation speeds, generator excitation voltage, generator phase currents and output voltages in general.
Keywords: micro – hydroelectric power plant, model, HydraulicTurbine and Governor (HTG) unit, rotor rotations, generator excitation voltage, generator phase currents and output voltages.
Аннотация. Разработана модель совместной работы микро – ГЭС и объекта геотермальной воды, с учётом их основных технико-технологических характеристик в широком диапазоне эксплуатационных условий, в том числе скорости вращения ротора, напряжение возбуждения генератора, фазные токи генератора и выходные напряжения в целом.
Ключевые слова: микро – ГЭС, модель, блок HydraulicTurbine and Governor (HTG), вращения ротора, напряжение возбуждения генератора, фазные токи генератора и выходные напряжения.
The microelectric power plant model consisting of a hydraulic turbine and a synchronous generator is shown in Fig.1. The Hydraulic Turbine and Governor (HTG) unit is a model of a hydraulic turbine with a control system. The control system includes a proportional differential (PID) controller and a control servo motor [1]. The general scheme of the model is shown in Fig. 2.

Fig.1. microGES model

Fig. 2. Model of the control system
The required values of angular rotation speed (wref) and power (Pref) are fed to the first two inputs of the unit. The third and fourth inputs of the unit receive the actual values of the angular rotation speed (we) and active power (Pe). The fifth input is supplied with the deviation of the angular rotation frequency of the synchronous generator rotor (dw). The output signals are the mechanical power that must be supplied to the corresponding input of the synchronous machine unit (Rm), and the value of the hydraulic turbine gate opening (gate). Inputs 2 and 4 may remain unconnected if a signal about the shutter position is used as feedback, and not a speed deviation. Ice input and output values are measured in relative units.
The hydraulic turbine itself is modeled by a nonlinear system shown in Fig. 3.

Fig. 3. Hydraulic turbine model
The servomotor controlling the turbine gate is modeled by a second-order system (Fig.4).

Fig. 4. Servomotor model
The window for setting parameters of the Hydraulic Turbine and Governor (HTG) block is shown in Fig.5.

Fig.5. Window for setting parameters of the Hydraulic Turbine and Governor block
Unit parameters (HTG) :
Servo-motor [Ka () Ta (sec)]:
[Servo motor parameters] Parameters of the servo motor model: gain Ka and time constant Ta.
Gate opening limits [gmin, gmax (pu) vgmin, vgmax (pu/s)]:
[Gate control limits gmin, gmax (o.e.) vgmin, vgmax (o.e./c)]. The maximum and minimum values of the shutter coordinate are gmin, gmax (o.e.), as well as the maximum and minimum values of the shutter speed vgmin, vgmax (o.e./c).
Permanent droop and regulator [Rp () Kp () Ki () Kd () Td (s)]:
[Controller Parameters]. The transmission coefficient in the feedback circuit of the regulator Rp, the gain coefficients of the proportional (Kr) and integral (Ki) parts of the PID controller, the gain coefficient (Kd) of the real differentiating link of the PID controller and its time constant (Td).
Hydraulic turbine [beta () Tw (sec)]:
[Parameters of the hydraulic turbine beta () Tw (c)]. The damping coefficient of the deviation of the angular rotation speed beta and the time constant of the model of the hydraulic part of the turbine Tw (c).
Droop reference (0-power error, 1 -gate opening):
[Type of feedback]. Sets the type of feedback signal: 1 – shutter position, 0 – deviation of electrical power.
Initial mechanical power (pu):
[Initial value of mechanical power (OE)].
The window for setting the parameters of the synchronous generator unit and the synchronous generator excitation system are shown in Fig. 6 and 7.

Fig.6. Window for setting parameters of the synchronous generator block

Fig. 7. Window for setting parameters of the synchronous generator excitation system unit

Fig. 8. Window for setting load parameters

Fig. 9. Window for setting parameters of the amplifier unit
The simulation results are shown in Fig. 10—14.

Fig. 10. Rotor speed

Fig. 11. Generator excitation voltage

Fig. 12. Phase currents of the generator

Fig. 13. The output voltage of the phase from the generator in relative units

Fig. 14. The output voltage of the phase from the generator in named units
Based on the results of software processing of the computational model of the joint operation of a micro – hydroelectric power plant and a geothermal water object, the authors obtained the main indicators of the rotor speed, the excitation voltage of the generator, the phase currents of the generator, the output voltage of the phase from the generator in relative units in order to predict the effective operation of the micro – hydroelectric power plant being developed.





